
Covert listening devices, bugs, wires, call them what you like, but these devices are commonly used in surveillance and espionage to gather intelligence from eavesdropping on private conversations.
A bug could be something purpose made, or it could be something as ordinary as a cellphone. And it is bugs that use the cellphone frequencies that are the most common and widely available. The bug could be disguised as an item found in an office such as a plug socket, USB key or phone charger. Using a concealed microphone, they covertly transmit sound or video back to the operator via the cellular network.
A regular cellphone can also be used willing or unwillingly to transmit conversations. An insider with their phone connected to their handler’s phone would be able to broadcast any conversation they were involved with. But cellphones can also be unwittingly hacked by nefarious actors and activated without the owner’s knowledge or permission. It is for these reasons that many TSCM monitoring solutions focus on detecting and restricting cellphone frequencies inside secure facilities.
There are some great Wireless Intrusion Detection Systems (WIDS) on the market that can alert to the presence and location of a GSM/UMTS phone and even identify the IMEI number. Some also have the capability to detect Wi-Fi and Bluetooth transmissions too. This is great if your only concern is threats from the cellphone network and you want to enforce a “no phone zone”. But what if those looking to exfiltrate information from your facility aren’t using off the shelf devices and are exploiting different parts of the RF spectrum?
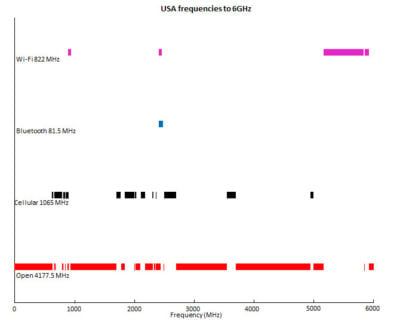
Most WIDS have a frequency range of about 600MHz to 6GHz and will only be looking at the part of the network used for Cellphone/Wi-Fi/Bluetooth. You can see on the chart in red how much of the spectrum is open and is potentially un-monitored. A well-equipped, state funded actor could bypass your security systems by using a different part of the spectrum. And if they are transmitting at frequencies higher than 6GHz, the WIDS system wouldn’t even be able to see it.
So, is a physical sweep the answer? A good TSCM sweep team should be able to detect bugs operating at higher frequencies even if they are not broadcasting. However, a bug placed after the sweep team have left won’t be detected. And as TSCM sweeps can be extremely disruptive and time consuming, it wouldn’t be something that could be performed every day.
The answer is to have a layered approach to security.
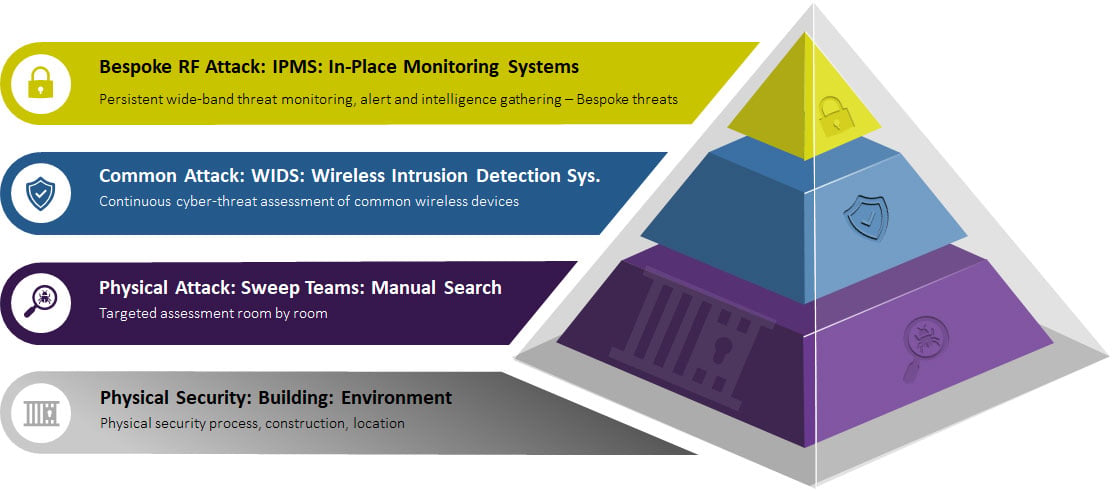
- Layer one is physical security
- Ensuring there are appropriate locks on doors, guards checking who comes and goes, or even designing the building with TSCM in mind
- Layer two is to conduct TSCM sweeps
- Periodic sweeps of key areas will pick up the hard-to-find bugs by manually searching room-by-room. This approach can be used across all layers.
- Layer three is to install a WIDS cellphone detector system
- Enforcing a “no phone zone” or detecting off-the-shelf bugs
- Layer four is to install an RF wide band In-Place Monitoring System (IPMS)
- Detecting bespoke transmissions that take place over a wide frequency range
An IPMS such as RFeye Guard can help protect a facility by detecting and locating bespoke RF threats, and not just Wi-Fi, Cellular and Bluetooth transmissions. RFeye Guard monitors the RF spectrum over a broad frequency range (up to 40GHz) to detect a wide variety of unauthorized transmissions. The highly sensitive receivers can detect low powered signals and those deliberately trying to hide in the noise or amongst other signals. As in-place monitoring systems are permanently installed, as soon as a device starts to transmit, it will be detected and security alerted.
Monitoring cellular network frequencies is important in combating illicit surveillance, but it shouldn’t be the only thing that is monitored. Adversaries are smart, and they are continually devising novel ways to infiltrate bugging devices and exfiltrate the information. By only covering the basics, organizations could be leaving their critical, secret information exposed. An integrated, layered approach to TSCM will ensure that secrets remain secret and the integrity of the facility is protected.
If you are interested in learning more about how an in-place RF monitoring system could benefit your organization, please get in touch.
