
ADS-B Basics
Automatic dependent surveillance-broadcast (ADS-B) is a surveillance technology currently being introduced in the US (Next Generation Air Transportation System), Europe (Single European Sky ATM Research) and across the globe. It functions as a replacement for secondary surveillance radar, and possibly even to replace primary radar in future, for air traffic monitoring and control. It requires planes to determine their current position using GPS, and then to broadcast the details of this position (ADS-B OUT). This information can then be used by air traffic control to coordinate the movement of planes through their airspace. Planes may also carry an onboard receiver (ADS-B IN), which allows them to receive the ADS-B OUT transmissions of other planes in the vicinity.
ADS-B Message Format
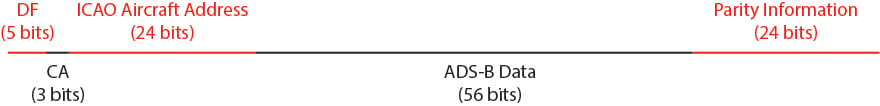
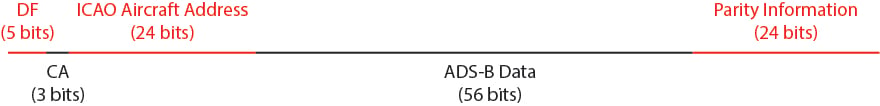
ADS-B messages consist of 112 bits of data, with five main subsections. These are:
Bits 33-88 contain the bulk of the transmitted information. Bits 33-37 (the type code) let the receiver know what kind of information is encoded in bits 38-88 – this could be aircraft identity, surface position, airborne position, airborne velocity, aircraft status, target state or aircraft operation status.
ADS-B message format broken down by section
ADS-B messages consist of 112 bits of data, with five main subsections. These are:
- Downlink Format (DF)
Bits 1-5 of the transmission give details of the transmitting system. DF values of 17 (10001 in binary) are associated with Mode S transponders (which can both send and receive signals), while DF values of 18 (10010) denote non-transponder based TIS-B systems, which cannot receive signals, and therefore can’t be interrogated.
- Capability (CA)
Bits 6-8 give additional detail about the capability of the Mode S transponder.
- ICAO Aircraft Address
Bits 9-32 encode the address assigned to the Mode S transponder in each aircraft. This can be used to uniquely identify the aircraft sending the signal.
- Data (including Type Code)
Bits 33-88 contain the bulk of the transmitted information. Bits 33-37 (the type code) let the receiver know what kind of information is encoded in bits 38-88 – this could be aircraft identity, surface position, airborne position, airborne velocity, aircraft status, target state or aircraft operation status.
- Parity Information
Bits 89-112 are used to confirm that the preceding information has been received correctly.
ADS-B message format broken down by section
Security Vulnerabilities
ADS-B is an attractive solution for air traffic control management for a number of reasons. Receiving stations can be built in almost any location, which means that ADS-B does not suffer from the problem of black spots in remote locations where building radar stations is unfeasible. Increased accuracy of location data (from more regular broadcasts of position) allows for smaller minimum aircraft separations, and therefore higher capacity. And as already described, it allows for plane-to-plane communication of position. However, it also has a number of potential drawbacks that need to be considered.
ADS-B is an unencrypted system, which means that anybody with the necessary equipment can receive and decode ADS-B signals. This possibility is used in a harmless (and indeed, useful) way by websites such as FlightAware, which plot (almost) live position updates of commercial aircraft.
Using ADS-B for air traffic control relies upon being able to receive transmissions sent by aircraft that could be many miles away from the receiving ground station. This means that even a relatively low-power jamming device located close to the ground station could be used to block incoming ADS-B signals.
An additional possibility is that because ADS-B transmissions are unauthenticated, spoof ADS-B signals can be generated. By creating a signal that matches the required messaging protocol, details of a non-existent ‘ghost’ aircraft can be sent to either ATC ground stations or to other planes. This could cause major disruption if flights need to be diverted to avoid the ghost aircraft. Moreover, it is possible to create multiple ghost signals simultaneously, greatly increasing the possible disruption. Malicious (and potentially state-sponsored) actors can effectively flood the airspace with thousands of fake planes, making ADS-B functionally unusable.
Using 3D TDOA
3D TDOA, performed using CRFS’s RFEye Nodes, can be a useful tool when dealing with these ADS-B vulnerabilities. Using a network of at least four Nodes, the position of the source of radio transmissions can be determined in 3D. In the case of ADS-B jamming, the jammer itself can be quickly located, allowing the relevant authorities to investigate and shut it down.

When dealing with the ‘ghost’ aircraft, 3D TDOA allows us to determine whether the signal actually originates from the location it purports to, based on the ADS-B encoded information. In cases where there is a disparity between the two location determination methods, air traffic controllers can be alerted, and investigation of the signal source can be carried out. And because 3D TDOA allows determination of altitude and velocity, it is straightforward to differentiate between signals from aircraft, and spoof signals being sent by a stationary ground-based source.
In addition, the Nodes that are being used for ADS-B spoofing detection are the same hardware required for detecting drones, so one system can be used to deal with multiple operational issues at airports.
Want to Know More?
Get in touch with us here at CRFS, and one of our team will be happy to help. If you would like to find out more about how 3D TDOA works, then download our 3D TDOA White Paper here.
